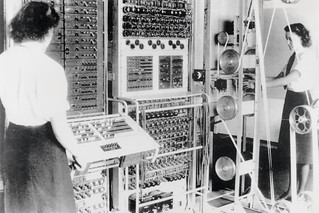
 This is the first of three articles about girls and women in Computing.
This is the first of three articles about girls and women in Computing.
On March 8th it was International Women's Day.
 This is the first of three articles about girls and women in Computing.
This is the first of three articles about girls and women in Computing.
On March 8th it was International Women's Day.
 At last! Or, to use the vernacular, woo hoo! The latest edition of the Digital Education ezine is now out. It contains a round-up of products seen at Bett, articles on girls and women in technology, loads of links and book reviews. Here’s a detailed list of the contents:
At last! Or, to use the vernacular, woo hoo! The latest edition of the Digital Education ezine is now out. It contains a round-up of products seen at Bett, articles on girls and women in technology, loads of links and book reviews. Here’s a detailed list of the contents: What’s the connection between Ada Lovelace, Charles Babbage, and me? Well, it’s a bit tenuous. Apart from the obvious, that we all liked computing (in effect), it is that they appear in a new graphic novel, and I love graphic novels.
What’s the connection between Ada Lovelace, Charles Babbage, and me? Well, it’s a bit tenuous. Apart from the obvious, that we all liked computing (in effect), it is that they appear in a new graphic novel, and I love graphic novels. Like many Englishmen, the most important thing to me is having a decent cup of tea. So I was delighted when we bought a variable temperature kettle. This doesn’t just heat up the water to boiling point. It lets you select the right temperature for the kind of drink you have. But how does it work?
Like many Englishmen, the most important thing to me is having a decent cup of tea. So I was delighted when we bought a variable temperature kettle. This doesn’t just heat up the water to boiling point. It lets you select the right temperature for the kind of drink you have. But how does it work? I’ve long been an ardent advocate of spreadsheets. They can be an invaluable tool in business, education or any other field in which planning, cost or both are paramount. As far as Computing and ICT is concerned, they can be used for teaching modelling and computational thinking. However, they have been denigrated as being “just” an office tool, far removed from the exciting world of coding or robotics.
I’ve long been an ardent advocate of spreadsheets. They can be an invaluable tool in business, education or any other field in which planning, cost or both are paramount. As far as Computing and ICT is concerned, they can be used for teaching modelling and computational thinking. However, they have been denigrated as being “just” an office tool, far removed from the exciting world of coding or robotics. I thought these posts from the archives might be interesting: 6 ideas for teaching the Computing curriculum. Unfortunately, being mathematically challenged, I originally inadvertently designated two of them as “#2”. That’s why I never became a maths teacher. However, I have since renumbered them, so they start at zero, which is, computationally speaking, a pretty good thing to do. Anyway, although the series refers to the “forthcoming Computing curriculum”, the ideas themselves are still useful I believe. I hope you agree.
I thought these posts from the archives might be interesting: 6 ideas for teaching the Computing curriculum. Unfortunately, being mathematically challenged, I originally inadvertently designated two of them as “#2”. That’s why I never became a maths teacher. However, I have since renumbered them, so they start at zero, which is, computationally speaking, a pretty good thing to do. Anyway, although the series refers to the “forthcoming Computing curriculum”, the ideas themselves are still useful I believe. I hope you agree. If, like me, you enjoy reading comics and graphic novels, and are interested in Computing, you may already be familiar with the blog called 2D Goggles Or The Thrilling Adventures of Lovelace and Babbage. This relates the story of the development of the Difference Engine and other aspects of the lives of Ada Lovelace and Charles Babbage. Their adventures are based on (mostly) real events and episodes, with a lot of poetic licence thrown in! I thoroughly recommend reading the adventures, and I suggest encouraging your students to do so too. It will help them learn about the development of computing and computer programming in an enjoyable way.
If, like me, you enjoy reading comics and graphic novels, and are interested in Computing, you may already be familiar with the blog called 2D Goggles Or The Thrilling Adventures of Lovelace and Babbage. This relates the story of the development of the Difference Engine and other aspects of the lives of Ada Lovelace and Charles Babbage. Their adventures are based on (mostly) real events and episodes, with a lot of poetic licence thrown in! I thoroughly recommend reading the adventures, and I suggest encouraging your students to do so too. It will help them learn about the development of computing and computer programming in an enjoyable way. At the end of the article 7 Characteristics of a good Computing Scheme of Work I said that people should work with other people on their Computing scheme of work. Why?
At the end of the article 7 Characteristics of a good Computing Scheme of Work I said that people should work with other people on their Computing scheme of work. Why? Now that the new Computing curriculum in England has been running for nearly a term, it's a great time to stand back and take stock. Actually, I recommend doing that even if you are not in England and/or have not needed to change anything. Here's a list of 5 questions you might care to ask yourself:
Now that the new Computing curriculum in England has been running for nearly a term, it's a great time to stand back and take stock. Actually, I recommend doing that even if you are not in England and/or have not needed to change anything. Here's a list of 5 questions you might care to ask yourself: I thought it would be interesting to dig out my scheme of work for Information Technology – as it was then then – from 1997. It was based on the Informatics scheme of work published by the now defunct organisation Acitt. Acitt was a subject association for ICT Co-ordinators. I helped to shape the Acitt scheme of work, but the one I used myself was a variation, adjusted to meet the circumstances pertaining to my school. I’ve reproduced it below.
I thought it would be interesting to dig out my scheme of work for Information Technology – as it was then then – from 1997. It was based on the Informatics scheme of work published by the now defunct organisation Acitt. Acitt was a subject association for ICT Co-ordinators. I helped to shape the Acitt scheme of work, but the one I used myself was a variation, adjusted to meet the circumstances pertaining to my school. I’ve reproduced it below. The Hour of Code allows anyone to try out coding for the first time by teaching the basics of computer programming in just sixty minutes.
The Hour of Code allows anyone to try out coding for the first time by teaching the basics of computer programming in just sixty minutes. With a new Computing curriculum that focuses on students learning to code and writing simple programs it’s important for school ICT and Computing heads, teachers or those responsible for ICT/Computing to make sure their school network is secure and able to handle the new requirements without compromising the rest of the system.
With a new Computing curriculum that focuses on students learning to code and writing simple programs it’s important for school ICT and Computing heads, teachers or those responsible for ICT/Computing to make sure their school network is secure and able to handle the new requirements without compromising the rest of the system.
Here are a few considerations to help with that and make sure your data is safe and the students can enjoy exploring new learning securely.
 Are your students yawning, checking their email, launching paper aeroplanes in your lessons? Perhaps you’re making one of these mistakes.
Are your students yawning, checking their email, launching paper aeroplanes in your lessons? Perhaps you’re making one of these mistakes. In this series I’m going to be making some suggestions, putting out some ideas. These are based on presentations I’ve given. I can think of how these ideas, or their implications, might be applied in the classroom. However, I think it better if I stand back and let you do that part of the work!
In this series I’m going to be making some suggestions, putting out some ideas. These are based on presentations I’ve given. I can think of how these ideas, or their implications, might be applied in the classroom. However, I think it better if I stand back and let you do that part of the work! I had the pleasure of attending one of the RM Technical seminars recently, and it was well worth the time. The event was divided into several strands. I chose the Curriculum and E-safety option rather than one of the more technical ones.
I had the pleasure of attending one of the RM Technical seminars recently, and it was well worth the time. The event was divided into several strands. I chose the Curriculum and E-safety option rather than one of the more technical ones.
As well as a very entertaining keynote lecture by Sir Ranulph Fiennes, there were three sessions:
(c) Terry Freedman All Rights Reserved